VoIP Security
VoIP Hacking: How It Works & How to Protect Your Restaurant VoIP Phone System

VoIP Hacking
VoIP phone systems differ from traditional setups because you don’t need copper wiring that spans across your entire office. Connections are made virtually using an internet connection. But that often causes security a big concern: everything is hosted in the cloud. Hacking a phone system isn't as far-fetched as you might think.
The Internet of Things revolution means everything is done online. The phone system makes it challenging to verify callers and can springboard into new data breaches. Thus, social engineering is common.
Should someone use VoIP to carry out an attack, they can access sensitive customer data.
VoIP hacking is a type of attack that a person uses to infiltrate your business phone system. They can listen in on calls, rack up expensive bills, and steal sensitive information–both about your business and your customers.
Hacks usually happen when one of your employees accidentally gives information to a scammer. These types of social engineering scams account for 97% of all malware attacks.
Hackers target people working in customer service and in the Network Operations Center (NOC), acting as someone else. Staff can unknowingly give unauthorized access to the hacker, and they take control of your VoIP phone system.
Access to your business’ phone system can launch other attacks. For example, a VoIP hack could access the information to charge your customers credit card, impersonate your business, and access private customer information.
It’s important to stay current on the ways business phone systems are compromised and review the steps you and your provider can take to secure communications.
Five types of VoIP hacking
1. Unauthorized use
This type of attack is when hackers use your business’ phone system to make phone calls.
Hackers can use your phone system to use robocalling and auto-dialing software. People who answer the phone to your caller ID will hear a prerecorded message asking them to do something—such as enter their credit card number to “confirm their account.” It isn’t your business making the call, though. The hacker now has access to all of that information.
Hackers can also conduct fraudulent activity using your legitimate business phone service. Your caller ID will show when they’re making phone calls using your VoIP system. They can impersonate your company to scam customers out of their private information.
The worst part? Unauthorized use of your VoIP system can go undetected, especially if you’re taking a DIY approach to setup. Regularly check your call logs and history and set alerts if you go over a certain limit. That way, you’ll be notified of unauthorized use sooner than later.
2. Toll fraud
Toll fraud occurs when hackers make international calls to other devices. Toll charges for these long-distance phone numbers can be expensive and will be billed from your account. A staggering $27 billion is lost due to toll fraud, according to Trend Micro.
Attackers can target users and admins with phishing scams to gain unauthorized access to your VoIP system.
For example, hackers leave your finance team a voicemail that asks them to verify their banking information. Your employee doesn’t know the difference, so they return the phone call and give the verification codes—such as your phone system password or IP address.
The hacker then has information they can use to hack your VoIP phone system and make expensive long-distance calls.
3. Caller ID spoofing
When your phone rings and the caller ID appears, do you trust the number shown?
Caller ID isn't always a reliable way to verify the person calling you. Attackers can use fake caller IDs and leverage them in coordination with another attack, like social engineering.
Employees often place a high value on a caller's phone number or name. So, if they get a call from someone appearing to come from their VoIP provider, they might be fooled into exposing important information.
Giving that information, often without realizing it’s not who you expected on the other end, can give hackers access to your business’ VoIP system.
4. Eavesdropping
Do you take payments over the phone, or ask customers to call you to give personal information? If so, you’ll want to prevent eavesdropping. This is when hackers listen in on your real-time business phone calls or recordings like voicemails.
Eavesdropping is only possible when the connection is unencrypted or the local network itself is breached. Insecure Wi-Fi networks—those without Transport Layer Security (TLS) and Real-time Transport Protocol (SRTP) — can invite attackers to monitor the network.
Eavesdropping allows hackers to collect information on your business and your customers. They can access every interaction your business has had.
Depending on the conversations they listen to, there’s a risk of hackers:
- Selling your customers’ private information
- Selling proprietary information to your competitors
- Bribing your business or customers. For example, they might ask for a cash sum to keep the recordings private, depending on the nature of the call.
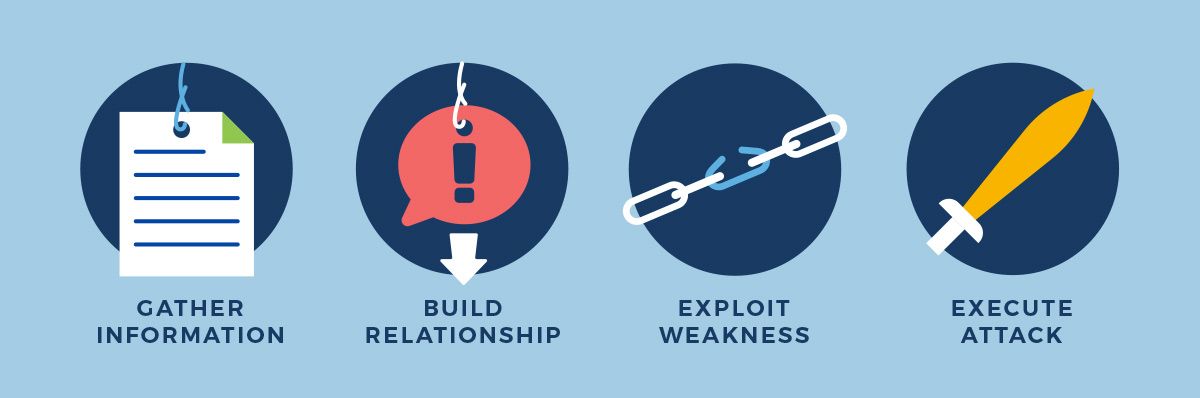
5. Social engineering
Research shows that 62% of businesses experienced a social engineering attack in 2018. It’s a common type of VoIP hack because it preys on people, not technology.
Hackers try to build relationships with their victims so they think it’s a genuine call, but it’s not. The call is a hacker impersonating someone else to trick you into handing over sensitive information. Social engineering is used by attackers because they prey on the fact that people genuinely want to be nice. It's uncomfortable to say no when someone asks for something—especially if you’ve got no reason to doubt who they say they are.
There’s also a lack of awareness around social engineering campaigns. Employees are rarely educated about the risks of fraudulent phone calls from attackers disguising a caller ID.
Attackers prey on people to extract information about a target that can be used for later. This can include false account requests, like verifying your account, and harassing or threatening victims based on the data they’ve acquired.
These emotionally-charged situations pressure staff into doing something right now, and that going against proper procedure is the right thing to do.
It's a jungle out there. Protect your VoIP infrastructure with SENTRY

Introducing SENTRY
SENTRY is a revolutionary new VoIP security platform. Designed by the experts at SYSTM to protect any on-premise, SIP enabled PBX, SENTRY provides carrier grade security technologies, delivered in a simple, fully automated appliance.